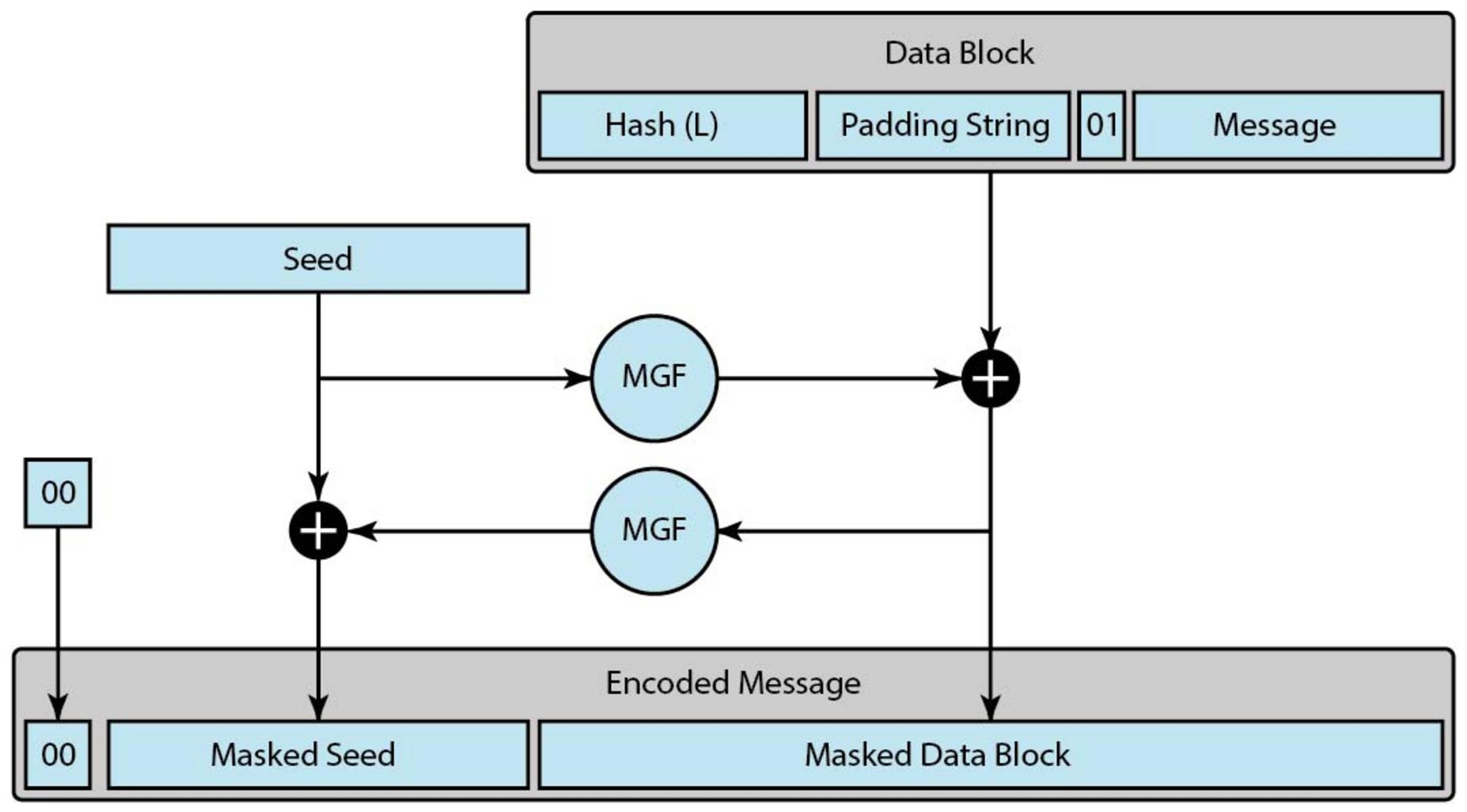
How Do Online Criminals Acquire Sensitive Data, Companies today gather and store vast amounts of user data.
A large portion of it is about private data that was previously solely retained by financial and medical institutions.
Threat actors, for instance, can get data by exploiting flexible eCommerce websites and applications.
Top Data Science Applications You Should Know 2023 (datasciencetut.com)
How Do Online Criminals Acquire Sensitive Data
What can companies do to protect the data of their users?
What are the most typical ways that user data is compromised, and how can that data be shielded from hackers?
Ransomware
A bad actor can use malware—harmful software that harms an organization—after gaining access to the system. A form of malware known as ransomware encrypts data in order to demand payment in exchange for the decryption key.
Depending on the ransomware type, the infection may lock particular files, grant hackers access to the data, or even prevent users from using the entire infrastructure.
How widespread is ransomware globally?
Sixty-six percent of businesses globally claim to have fallen victim to this type of virus. The nation with the most number of ransomware cases in Australia.
Several high-profile ransomware attacks, including those involving Australian businesses, have occurred in 2022.
The 10 million subscribers’ data was exposed as a result of the X company’s data breach. The information was sensitive in a lot of ways.
Another significant ransomware incident, ‘Y Bank’, resulted in 9.7 million people having their data exposed.
Both businesses declined to pay the ransom and, along with it, declined to support additional illegal conduct.
Boosting in Machine Learning:-A Brief Overview (datasciencetut.com)
Data mining
Data scraping is the practise of taking advantage of flaws in websites, usually social media platforms, to collect user names, email addresses, and phone numbers.
The information provided by the users is gathered and arranged in a spreadsheet as part of this hacking method.
For instance, data scraping recently affected widely known social media platforms also. In a recent post on breach forums, the hacker claimed to have obtained the data of 400 million people, many of whom were well-known figures.
In exchange for not selling the data they were able to scrape, the criminal requested cash. Email addresses, real names and usernames, phone numbers, and other details are among the information that the criminal possesses.
Applications of Data Science in Education – Data Science Tutorials
phishing tactics
Phishing is the primary way that most data breaches begin. According to estimates, this kind of social engineering is to blame for 90% of data breaches.
Hackers rely on the human aspect and take advantage of recipients of phishing emails who fall for their tricks in order to access the data.
Because individuals are frequently the weakest link in security, phishing has been effectively utilised for years and is still a common hacking technique.
They might not be able to spot a phishing email with a malware-infected attachment that got past filters without the proper training.
The sophistication of social engineering has increased, just like that of other hacking techniques.
There are numerous different phishing scams, and many of them are so sophisticated that they may trick even seasoned cybersecurity experts who are well-versed in the practice.
Others of them take place via phone calls, some over SMS messages, and some over email.
They all share the need for the victim to respond swiftly; frequently, they are looking for credentials obtained under the guise of the boss or other information that could help them and grant them access to the company’s system.
How to Prevent Cybercrime From Accessing Your Data
requiring secure passwords
regulating access based on a person’s position within the organisation
Utilizing AI-based security management technologies such as Threat Exposure Management
Weak passwords continue to be a serious problem that, if discovered by hackers, may result in data breaches.
Many of them are either too short, reused or contain details that can be used to identify the individual.
Role-based network access is crucial since a bad actor could get access to the entire system with just one stolen credential.
A program called threat exposure management inventory assets and evaluates systems to determine whether they are likely to be the target of successful hacking.
Additionally, it is crucial to have a backup of all the data that is crucial to the business. In the case of ransomware, backups allow teams to carry on working even if the hacker was able to access key data.
Top Reasons To Learn R in 2023 – Data Science Tutorials
The Best Way to Keep Data Safe is to Prevent Attacks
Some of the most frequent and harmful events that result in data being stolen and disclosed include ransomware, data scraping, and phishing.
It’s too late once the hacker posts that the data is available for purchase on forums dedicated to data breaches or discloses private user information.
Therefore, it’s crucial to insist on strong credentials that can’t be easily cracked and have several tools that safeguard the infrastructure that houses the large data in order to preserve the sensitive information that customers entrust to a company.
Finally, to keep up with the frequent changes in the cloud or any movement that could harm the data within the system, all of the technologies that protect the data must be managed on a regular basis.
Training employees, establishing security tools and standards, and routinely monitoring the company’s security are the keys to keeping data secure. The procedure is then repeated by the security teams.
Top Data Science Skills- step by step guide (datasciencetut.com)